UTS (Mar 2018 – Present)

The University Of Technology Sydney (UTS), is a public research university located in Sydney Australia. I am currently commencing my second year, completing my Bachelor of Engineering (Honours) – Diploma in Profession Engineering Practise, majoring in Software Engineering.
Applications Programming (High Distinction), and Data Structures & Algorithms (Distinction)
Key Learnings:
- Applying the core fundamentals of Java patterns and data structures to an actual application
- Introduction of object-oriented programming (OOP) and developing a comprehensive understanding of the topics behind OOP, such as inheritance and polymorphism
- Applying different algorithms to improve how an application can execute a task
- Obtaining an understanding of Big-O notation and the importance of time and space complexity when developing an application
Projects:
- A PC building application designed to explore the components required to build a PC
- Developed an application that implements algorithms on a directed graph data structure
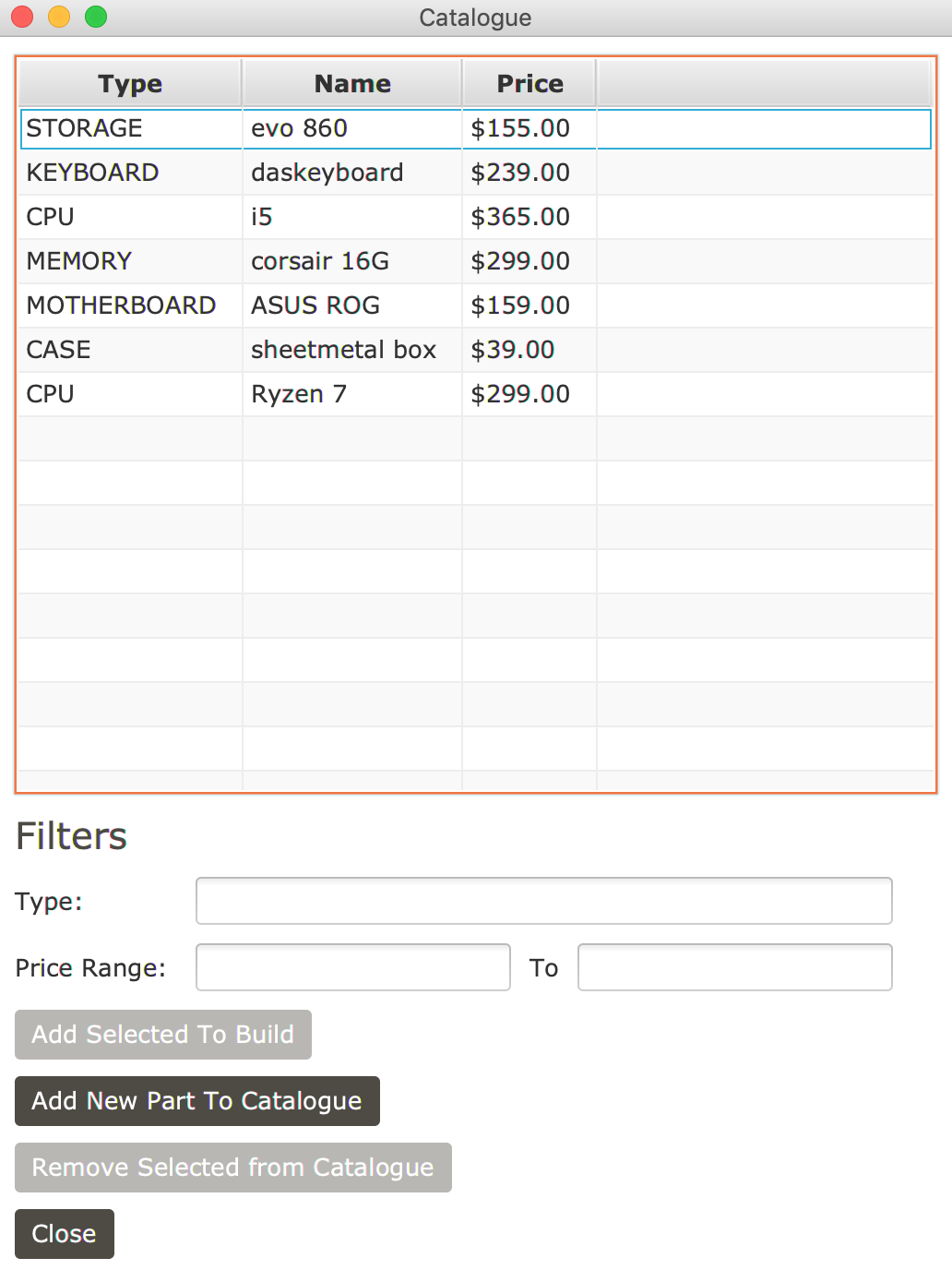

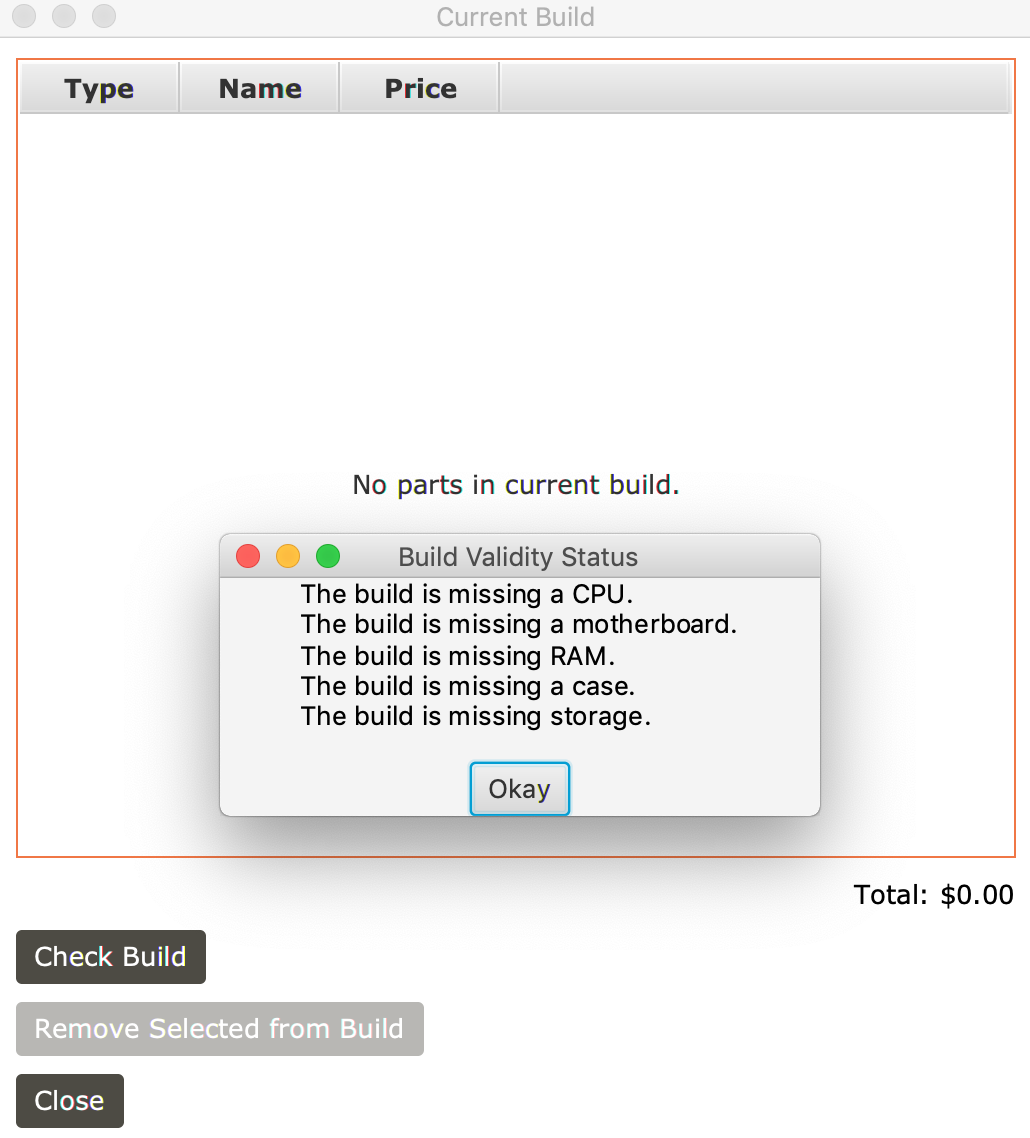
Development Details:
- IDE : NetBeans
- Language: Java, JavaFX
Software Studio (High Distinction) – Web Development
Key Learnings:
- Applying an agile methodology to the development of various software projects
- Developing an understanding of core software development tools such as GitHub and Jira
- Implementing technology stacks such as MERN (MongoDB, ExpressJS, ReactJS, NodeJS) in web-based applications
Projects:
- Web-based dating application that utilises machine learning to match users before they interact with each other
- Online E-commerce software website application
- Automatic student subject enrolment application
- Online anti-cheating system for student examinations that utilised facial recognition to authenticate a student’s identity
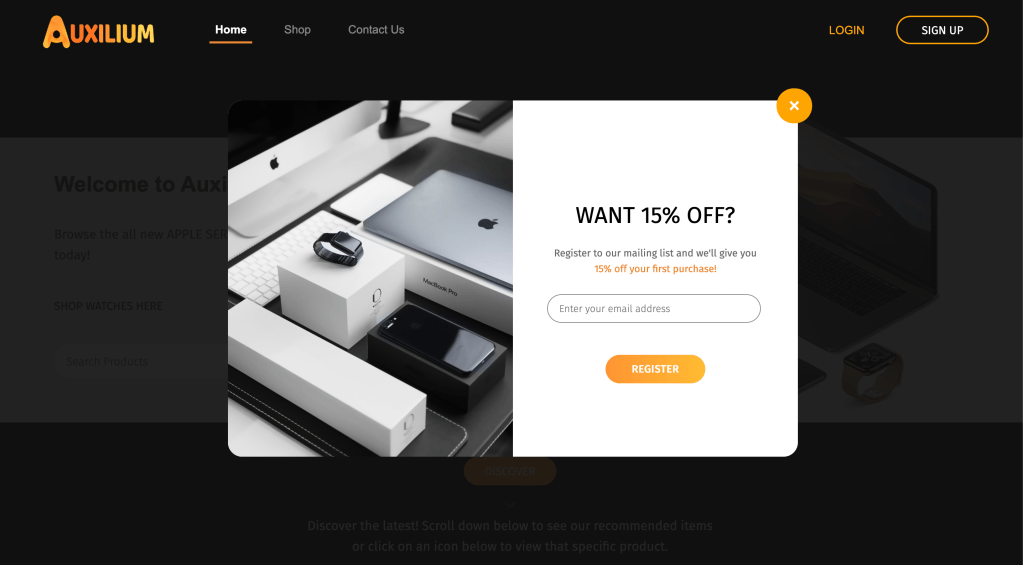
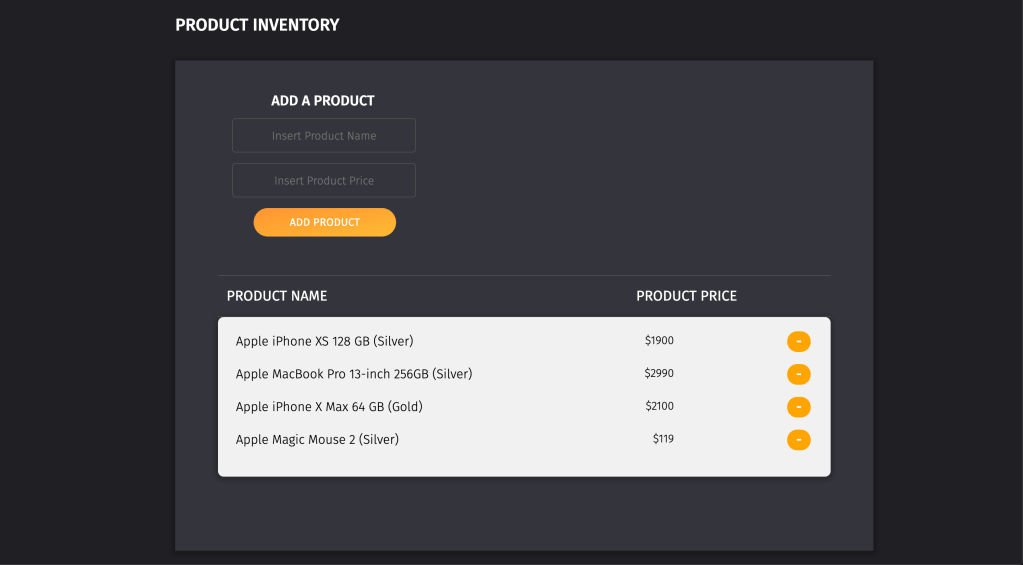
Digital Forensics (Distinction) – Cyber Security
Key Learnings:
- Analysing how to explore and restore data from a corrupt state and in a secure manner
- Familiarising the legal requirements associated with carrying out a forensics procedure
- Exploring different digital forensic processes such as order of volatility and chain of custody
Projects / Tasks:
- Applying various applications and command-line tools such as the XXD, file, EXIF tool commands to restore a corrupted image to its original state
- Recovering deleted files from an external disk / hard drive
- Monitoring web traffic and identifying malicious activity
